In the business world, the belief that ‘it won’t happen to us’ is more dangerous than reassuring. With hacker attacks occurring every 39 seconds and affecting one in three Americans annually, it’s alarming to note that 58% of these cyber attacks target small businesses.
| “In an era where cyber attacks and data breaches are becoming a daily headline, protecting your business is no longer an option but a necessity.” Nahjee Maybin, CEO of Kenyatta Computer Services. |
These attacks often translate to compromised client trust, daunting repair costs, and potentially, the end of the road for some businesses.
Are you doing enough to ensure your business isn’t next on the list? In this blog, we’ll introduce you to a cyber security assessment checklist designed for businesses. We’ll go through each point, highlighting areas where you might need to strengthen your security.
Common Causes of Security Breaches
Navigating the intricate maze of cybersecurity can be daunting. Before diving deeper into the checklist, it’s crucial to identify potential security breaches.
Here’s a quick glance at common causes, their potential aftermath, and preventive security measures to consider.
| Common Causes of Security Breaches | Potential Consequences | Preventive Security Measures |
| Phishing Attacks | Loss of sensitive data, Financial losses | Email filtering, Employee training, Regular security awareness sessions |
| Weak Passwords | Unauthorized system access, Data theft | Password management tools, Multi-factor authentication implementation |
| Outdated Software | Exploitation of known vulnerabilities | Regular software updates, Patch management services |
| Human Error | Accidental data exposure, Misconfigurations | Regular training, System audits, Setting up access controls |
| Insider Threats | Intellectual property theft, Corporate espionage | Monitoring systems, Employee behavior analysis, Strict access controls |
12 Steps Cyber Security Risk Assessment Checklist
1. Identify Vulnerabilities in Information Systems
Understanding your weak points is the first step in creating a robust defense.
By identifying vulnerabilities in your information systems, you can ascertain where potential cyber threats might infiltrate your infrastructure. Regular vulnerability assessments ensure that no chinks remain in your armor.
Worried about data breaches compromising your business?
See how we’ve consistently protected companies over the last 33 years.
2. Evaluate Your Access Controls
Your access controls determine who can access what within your business. Ensure that these controls are stringent, updated, and only grant access to those who truly need it. Unauthorized access is a leading cause of data breaches.
3. Prioritize Risks
Not all risks carry the same weight. By understanding and categorizing the potential threats, businesses can prioritize risks and allocate resources effectively. This ensures that the most critical threats are addressed first.
4. Security Controls Assessment
Analyze the efficacy of your current security controls. Are they robust enough to fend off current and emerging threats? Conducting periodic IT security assessments will ensure that your controls evolve with the changing cyber landscape.
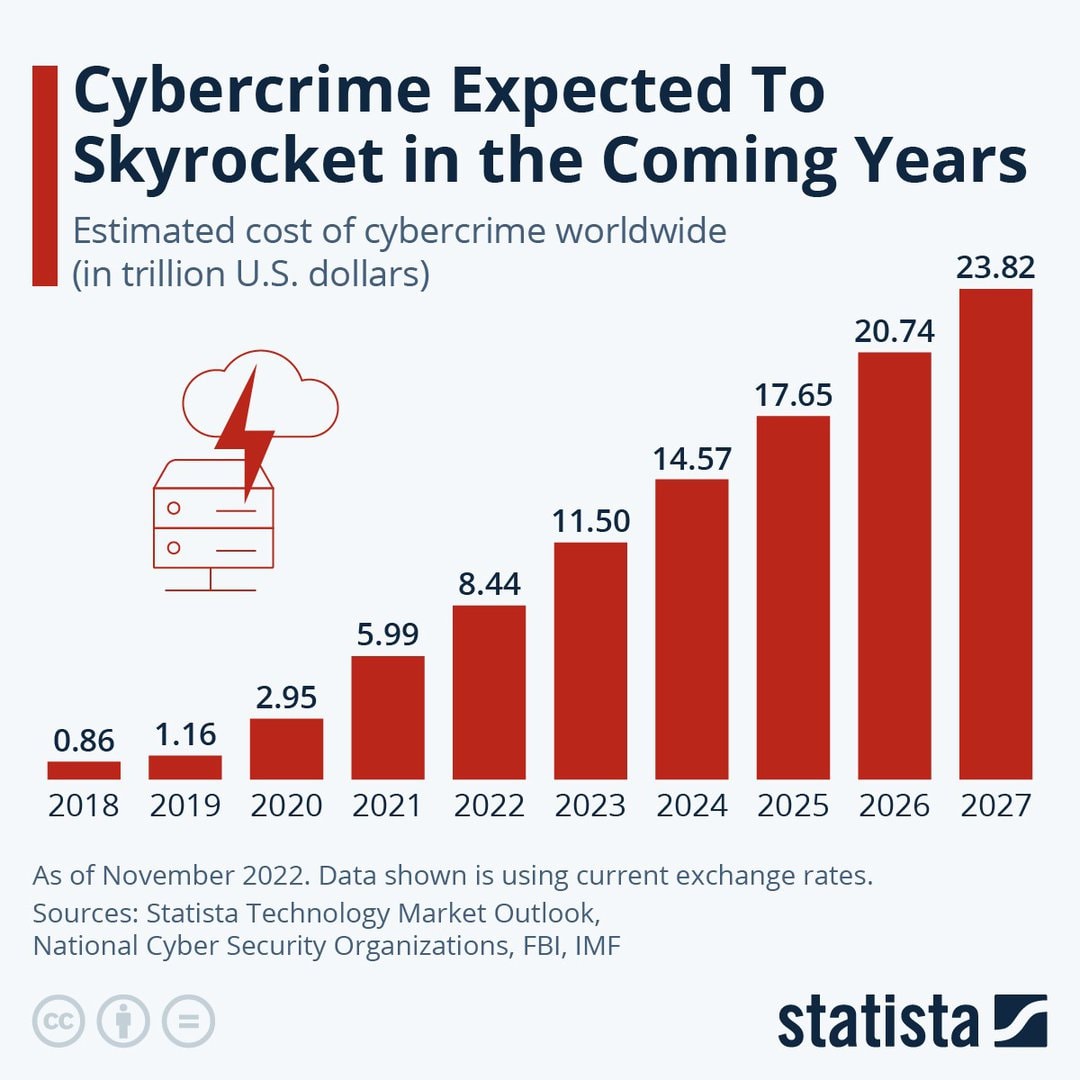
Source: Statista
5. Evaluate Human Error Potentials
While technology continues to advance, one consistent vulnerability remains, human error. Regardless of how sophisticated a system might be, a single mistake by an employee can jeopardize the entire network.
Employees often unintentionally become the gateway for cyber attacks, be it through mishandled sensitive information, clicking on malicious links, or using weak passwords.
Emphasizing the importance of cyber safety and investing in consistent training and awareness programs not only educates but also empowers employees.
6. Response Plan Adequacy
When a business faces a security incident, its ability to respond swiftly and effectively can greatly impact the aftermath, both in terms of potential damage and reputation.
In the unfortunate event of a security incident, having a coherent response plan in place is crucial. This plan should outline the steps to take, from notifying stakeholders to mitigating damage.
Peace of mind is just one click away
Begin your cybersecurity journey with us
7. Incident Response Protocol
Incident response protocols are crucial for businesses to manage and mitigate security incidents effectively. When we talk about detailing how the security team reacts to different types of breaches, we are essentially referring to a multi-faceted approach that takes into account the varied nature and impact of security incidents
Beyond having a plan, your incident response protocol should detail how the security team reacts to different types of breaches, ensuring swift action and minimal damage.
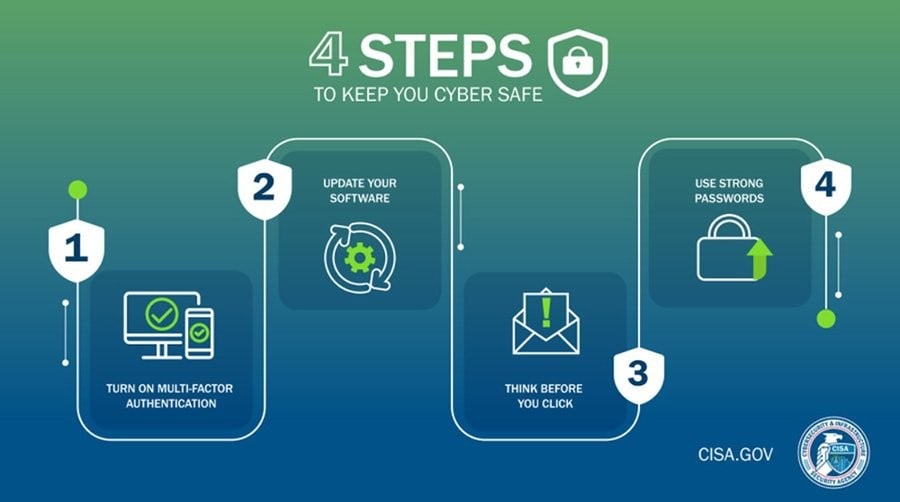
8. Multi-factor Authentication Implementation
Multi-factor authentication (MFA) is designed to verify the identity of users by requiring them to present multiple pieces of evidence or “factors” before granting access.
Multi-factor authentication adds an additional layer of security, ensuring that even if credentials are compromised, unauthorized access is prevented.
Source: TechTarget
9. Threat Assessment for Natural Disasters
Beyond man-made threats, natural disasters can also disrupt information systems. Evaluate your preparedness for events like floods, earthquakes, and fires, ensuring data safety and system uptime.
For instance, a business in California might be more concerned about earthquakes, while one in Florida might prioritize hurricane preparedness.
By understanding the risks, putting in place robust systems, and ensuring a culture of preparedness and regular testing, businesses can significantly mitigate the risks posed by natural disasters.
10. Review of Regulatory Requirements
Regulatory requirements related to cybersecurity have emerged globally as governments and industries recognize the importance of protecting digital assets and user data.
Depending on your industry and region, there might be specific regulatory requirements related to cyber security. Ensure your practices align with these standards to avoid legal repercussions.
11. Sensitive Information Protection
Proper storage and handling of sensitive information are paramount to ensuring its security and confidentiality.
Evaluate how you store and handle sensitive information. Implementing encryption and strict access controls ensures that even if data is accessed, it remains unintelligible.
Before doing that, it’s essential to define what “sensitive information” means in your context. It could be:
- Personal data: names, addresses, Social Security numbers.
- Financial data: credit card details, bank account numbers.
- Health records.
- Business secrets or intellectual property.
- Any other data that requires protection from unauthorized access.
12. Threat Assessment Checklist Cyber Security
Maintain a threat assessment checklist for cyber security that is regularly updated to reflect emerging threats and changes in your business operations.
Run mock drills and simulations to assess how your business would respond to real-life security threats, ensuring that everyone knows their role and responsibilities.
Secure Your Business’s Future With Kenyatta Computer Services
A single lapse in cybersecurity can result in irrevocable damage to a company’s reputation, finances, and client trust. Alarmingly, the smallest of oversights often lead to the most significant breaches.
With 33 years in business and boasting over 100 years of combined experience, Kenyatta Computer Services stands as a pillar of trust and expertise.
| Explore our range of IT services in Denver:
|
Our legacy lies not just in our years but in our commitment to taking a hands-on approach to security. Together, we can curate a cyber security risk assessment checklist that not only safeguards your data but also instills confidence.
Don’t leave security to chance.
Get help with your free threat assessment checklist for cyber security by contacting us today for more information.